Copyright © Network Control Center · All Rights reserved · E-Mail: admin@ncc2017.org
4649 Tanglewood Road
Jackson, MS 39201
Tel: 1-662-902-5682
Jackson, MS 39201
Tel: 1-662-902-5682
Suite 101, 1220 West Market Street
Wilmington, Delaware U.S.A. 19901
Tel: 1-302-123-7777
Wilmington, Delaware U.S.A. 19901
Tel: 1-302-123-7777
Blog
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Integer nec
odio. Praesent libero. Sed cursus ante dapibus diam. Sed nisi. Nulla
quis sem at nibh elementum imperdiet. Duis sagittis ipsum. Praesent
mauris. Fusce nec tellus sed augue semper porta. Mauris massa.
Vestibulum lacinia arcu eget nulla.

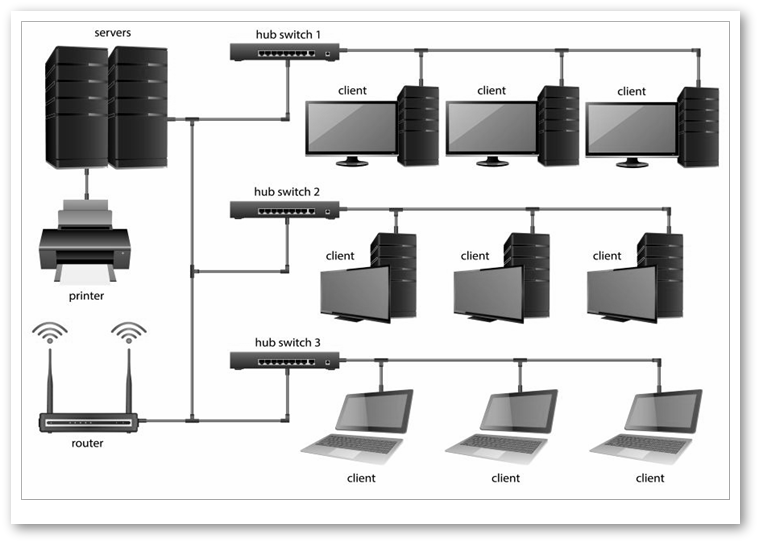


How to design a computer network from scratch
A skilled network design specialist will design your computer network in a way that helps it scale, and even transform,
according to your ever-evolving business objectives.
Another key goal is to ensure that the network is available all the time.
It is also important to build a network that is secure and can protect itself, fending off hackers and other automated tools
and bots that try to infiltrate it.
Finally, a well-built computer network should be managed without too much effort.
Everything starts with the step in which we identify network requirements. At this stage, we work closely with our
customers, finding out what are their main goals.
It's a two-step process.
First of all, we learn what are your business goals, and how your new computer network can help you achieve them.
Then, we implement the needed technologies that make it all possible.
Some businesses may already have a network in place. If this is the case, we gather information about the existing network
and its features.
Often times, some of the existing hardware can be used for the new network. We won't ask you to buy new equipment, if
the old one can be successfully reused.
We work using the proven top-down approach methodology. This means that we determine the needed applications and
services at the beginning, and then we start designing the network.


Suite 101, 1220 West Market Street
Wilmington, Delaware U.S.A. 19901
Tel: 1-302-123-7777
Wilmington, Delaware U.S.A. 19901
Tel: 1-302-123-7777


But is it possible to improve network efficiency, once that all the hardware is in place? The answer is a firm "Yes!" most of
the times. Existing network addresses and protocols may be changed to achieve this objective.
New security measures are being added.
New network services are implemented.
Servers may be relocated.
Wireless access may be added or improved in certain areas.
A key feature that many designers are overlooking is network traffic prioritization. This is often times ignored until
something bad happens. About 20 people are downloading that big-sized ppt in the meeting room at the same time, for
example, and all of the sudden the system can't take new orders from new clients. Or a server crashes and the entire sales
team is paralyzed!
The Network Control Center specialists work differently. We design your company's computer network in a way that isolates
the hardware that may fail.
Accidents can always happen, of course, but this doesn't mean that when a server goes down, all your employees will have
to wait until the problem is fixed.
We make sure that all critical hardware components utilize dual power supplies and redundant cooling fans. This increases
costs, but it's an investment that every responsible business owner should make.
And even when something bad happens, if the network is built using hot-swappable components, things can get back to
normal within minutes.
It's the ideal solution, because hardware can be plugged in or removed without having to power off the devices.
It's one of the most efficient ways of cutting down repair time, and thus disruption of network services.
Your network should be powered by uninterruptible power supply (UPS) devices. This way, any problems caused by potential
power outages are eliminated.
NCC provides training as well. Because humans can make computer networks fail as well! According to Gartner, about 40%
of network outages are caused by people who haven't received enough training.
However, at the end of the day, the safest solution is a full network backup strategy. Network redundancy is important as
well, of course. It's also an important way of reducing downtime.
Hardware-based firewalls help prevent network attacks. The firewall will examine each data packet, and then either forward
it to the network, or discard it, based on its source and destination addresses, the used protocol, the port number, and so
on.
While this isn't a component of the actual network design, we can also provide end-user security measures. Most of the
time, we are talking about antiviruses and anti-spyware applications which have stood the test of time, protecting their
users.
Making sure that only authenticated devices are able to access the network will limit other people's access to it. If the
network contains Wi-Fi components as well, it is critical to train your employees on how to minimize the unwanted wireless
access risks.
Of course, your network will not be safe if you don't take the needed measures to provide physical security in the first
place. If a villain can get access to the routers and switches, he could change passwords, and thus get full access to any
device on the network without effort.
Often times, networks are equipped with additional security devices, including motion detection sensors and cameras.